About Us
Unified platform. Complete protection. Designed with a Zero Trust philosophy and powered by artificial intelligence, the 918 Security Platform performs proactive monitoring, analysis, and prevention of sophisticated threats in real time with reduced complexity, enabling secure growth and innovation for your organization.
90% of cyber leaders who attended the Annual Meeting on Cybersecurity believe that inequity within the cybersecurity ecosystem requires urgent action.
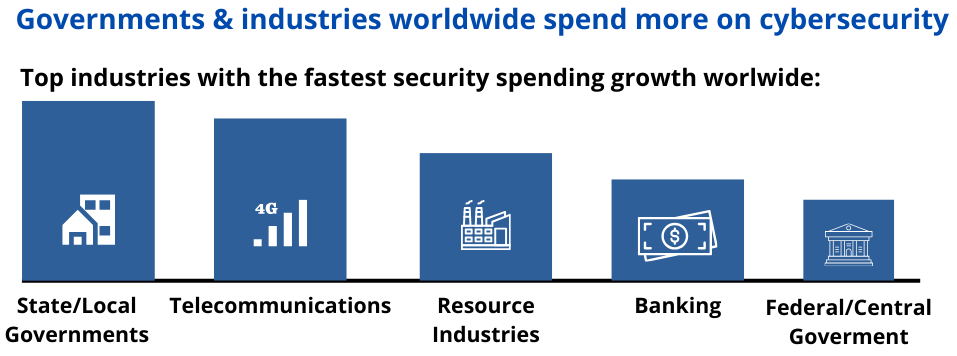
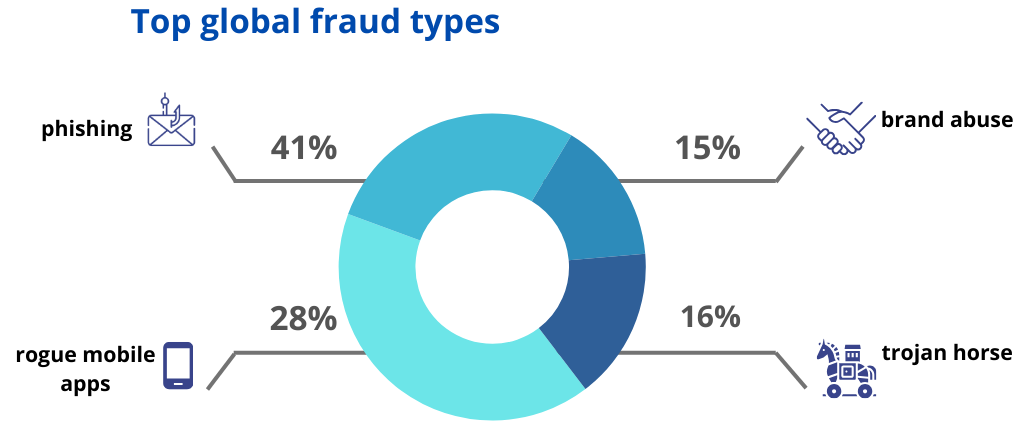
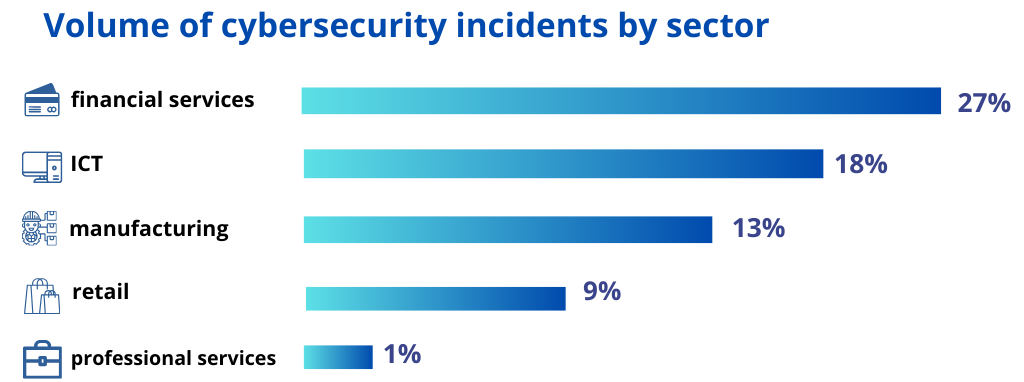
And about our methodologies and project phases?
Phases
Methodologies
Our methodological approach is based on internationally recognized security frameworks such as NIST, COBIT, and ISO 27001. We use a combination of proprietary technologies and solutions from leading market partners to provide robust and efficient protection.
How to find us
Address
Wilmington, Delaware.1209 North Orange Street,
info@918intelligence.com


